In our latest post we explained why you should consider enabling SSO for as much applications as possible. This post will explain how to Configure Gitlab to use SSO with ADFS.
Prerequisites
- Your own Gitlab server.
- ADFS 2012 R2 or 2016.
- The signing certificate thumbprint of your ADFS server.
- Some basic knowledge about claims.
Configure Gitlab
You have to modify the contents of your gitlab.rb file, usually located in /etc/gitlab/. Most important is that we configure the default ADFS claims to be used. That makes it easier to configure it in ADFS.
# Following settings are needed for omniauth (/saml)
# See https://docs.gitlab.com/ce/integration/saml.html for more information.
gitlab_rails['omniauth_enabled'] = true
gitlab_rails['omniauth_allow_single_sign_on'] = ['saml']
gitlab_rails['omniauth_auto_link_ldap_user'] = true
gitlab_rails['omniauth_auto_link_saml_user'] = true
gitlab_rails['omniauth_block_auto_created_users'] = false
# Configure omniauth the the correct provider.
gitlab_rails['omniauth_providers'] = [
{
name: 'saml', # This is the internal name of the omniauth provider
label: 'The button label',
args: {
assertion_consumer_service_url: 'https://git.yourdomain.com/users/auth/saml/callback',
idp_cert_fingerprint: '2c:4f:d3:ce:34:34:8b:80:...', # This is the signing certificate thumbprint
idp_sso_target_url: 'https://adfs.yourdomain.com/adfs/ls/',
idp_slo_target_url: 'https://adfs.yourdomain.com/adfs/ls/',
issuer: 'http://git.yourdomain.com', # This is the main url of the gitlab installation. (confusing name!)
name_identifier_format: 'urn:oasis:names:tc:SAML:2.0:nameid-format:persistent',
attribute_statements: {
username: ['http://schemas.xmlsoap.org/ws /2005/05/identity/claims/upn'],
email: ['http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress'],
name: ['http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name'],
first_name: ['http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname'],
last_name: ['http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname'],
}
}
}
]
# See https://github.com/omniauth/omniauth-saml#options for options.
# Automatisch redirect naar login scherm, skip this when testing!
# gitlab_rails['omniauth_auto_sign_in_with_provider'] = 'saml'
You’ll have to restart (or maybe reconfigure) gitlab in order to pickup the changes.
Configuring ADFS
Once you have changed the gitlab settings, you’ll be able to add Gitlab as a relying party by importing the metadata. The metadata is available at https://git.yourdomain.com/auth/saml/metadata. So go ahead and add Gitlab as a relying party.
For configuring the claims you can just go ahead and add a new Rule (Send LDAP Attributes as Claims).
- E-Mail-Addresses => E-Mail Address
- Given-Name => Given Name
- Surname => Surname
- Display-Name => Name
- User-Principal-Name => UPN
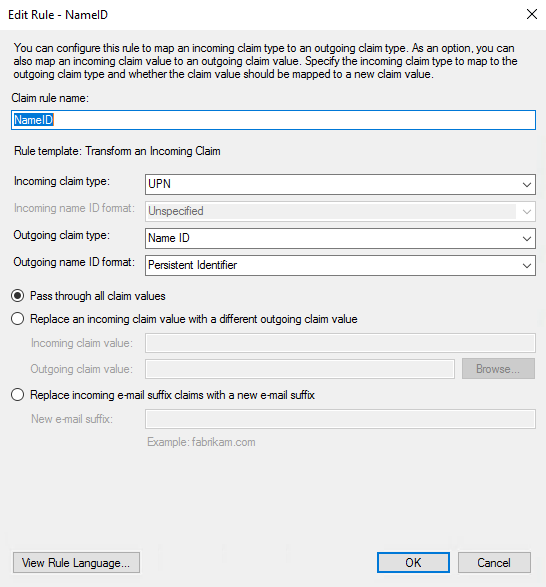
Then add an additional rule where you convert the UPN to the Name Identifier, add a new rule (Transform an Incoming Claim).
- Rule name: Convert UPN to Name ID
- Incoming claim type: UPN
- Outgoing claim type: Name ID
- Outgoing claim ID format: Persistent Identifier
- Pass through all claim values
All set
If you made it this far, you’re ready to test it out.
Still got any questions? Feel free to contact us.

0 reacties